The Rise of AI Malware: How to Protect Yourself
The Rise of AI Malware: How to Protect Yourself
AI Enthusiasts gradually become #1 target for cybercriminals
Over the years, malware operators have continuously adapted their strategies to capitalize on emerging trends and exploit new vulnerabilities. In the past, they primarily relied on distributing classic “keygen.exe” programs through platforms like YouTube, file sharing and custom fake websites, preying on users seeking free software or game access.
However, as technology has advanced and AI-related tools have gained popularity, cybercriminals have shifted their focus to more sophisticated methods. They now target users searching for AI services like OpenAI ChatGPT and Midjourney, as well as many other popular newly emerged AI solutions.
Criminals have found an AI Goldmine.
It’s evident that threat actors naturally shift into more “trending” topics to infect as many victims as possible while providing relevant fake content. However, not only have they found a steady way of generating traffic by adding the magic word “AI” to their fraudulent websites, but they have gone further and have found many ChatGPT or Midjourney’ users’ pain point.
Both of these AI services have gained immense popularity, but they lack dedicated standalone apps. Users access ChatGPT through a web interface, while Midjourney operates via Discord. This gap has been exploited by cybercriminals who direct AI enthusiasts to counterfeit web pages advertising phony apps.
Malware operators have been seen using Google Search ads, which lure users to dubious websites as part of a BATLOADER campaign aimed at spreading stealer malware such as RedLine and Vidar.
What is Stealer malware and how does it operate?
Stealer malware is a type of malware that is designed to steal sensitive information from infected systems. When executed, it typically searches for and collects data such as browser-saved login credentials, credit card information, browser history and cookies, cryptocurrency wallet access, desktop files, gaming credentials among other technical instance’s information and it even takes desktop screenshots.
This information is then sent back to the attacker’s command and control server, where it can be used for malicious purposes such as identity theft, financial fraud, or espionage. Cyber criminals often steal social media, gaming and other accounts to then re-sell them or use them for other kind of fraud, like social engineering.
Stealer malware can be distributed through various means, including phishing emails, malicious websites, and infected software downloads. Once installed on a system, it can operate in the background without the user’s knowledge, collecting data and sending it back to the attacker.
Most antivirus software can’t detect stealer malware.
At Kaduu we work with stealer logs on a daily basis and have conducted extensive research on the topic. Here we present the most common ways that this type of malware is spread. For our example, we have chosen the “RedLine” stealer, as it is currently the most prevalent and used by cybercriminals the most. It is designed for Windows OS only. However, stealer malware for Linux and Mac OS exist in the wild.
Top-3 ways RedLine malware is being disguised
1. “Cracked” software
It is often disguised in licensed software “cracks”. We can see on a screenshot that we have obtained from RedLine malware logs, that the owner of this computer has been searching for a free version of Microsoft Office. However, instead, he became infected:

We can report that the “AutoCad” software key generator has been relatively “popular” in Redline’s proliferation through YouTube videos:

2. Games or gaming-related software
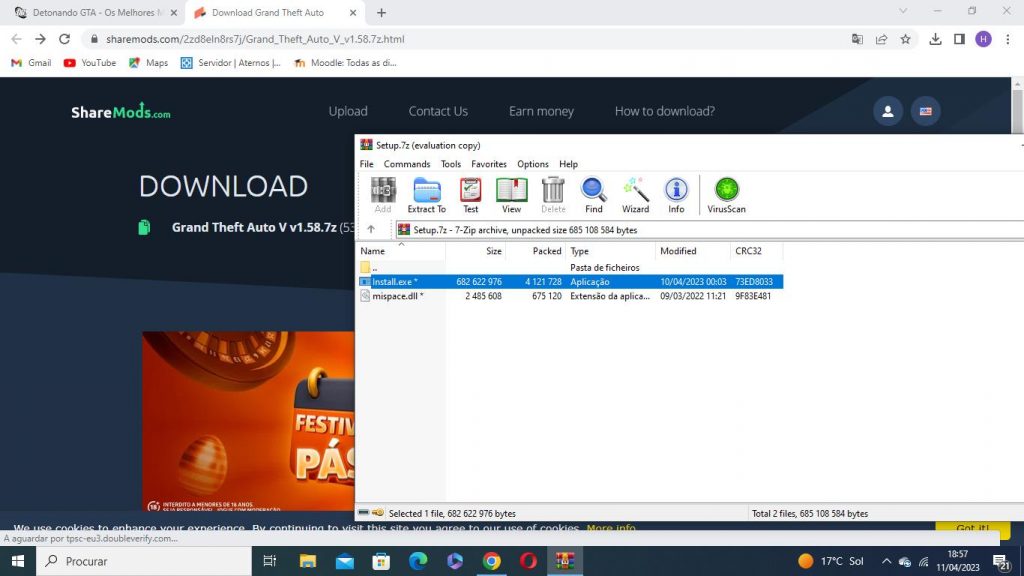
The stealer malware is often disguised as various games, for example, this victim on thescreenshot below tried downloading Grand Theft Auto, but received a computer virus instead:
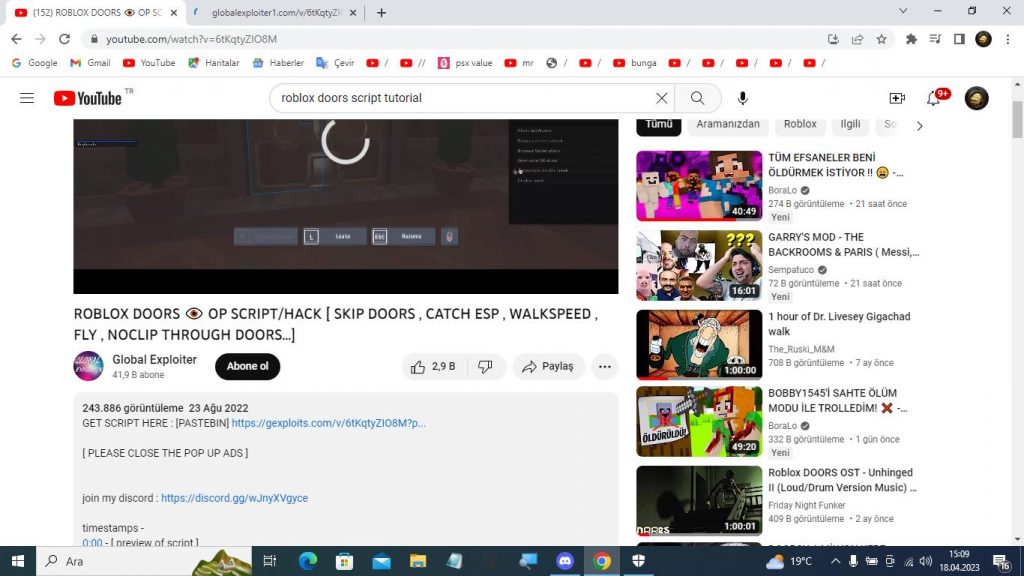
Stealer malware can also present itself as some game enhancements, like cheat codes, or game hacks. On the next screenshot we can see that the user has been interested in a script that would facilitate a game he probably plays:
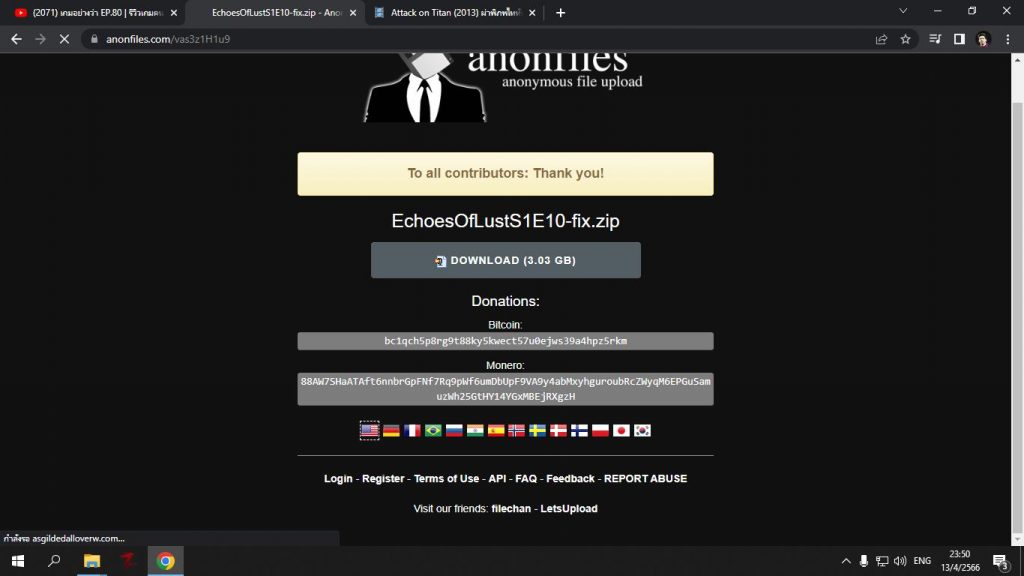
3. Adult content
Finally, RedLine is spreading online through adult content:
How to protect yourself?
To avoid falling victim to stealer malware, it is important to take proactive measures to protect your systems. This includes first and foremost, avoiding suspicious links and downloads. 3 crucial measures: keeping your OS and other software up to date; not saving any passwords in browsers memory and using reputable antivirus software to detect and remove malware. Additionally, it is important to stay vigilant and report any suspicious activity to your IT department or tocybersecurity professionals.
If you liked this article, we advise you to read our previous article about recent ransomware attack on the Department of Education of the Canton of Basel-Stadt. Follow us on Twitter and LinkedIn for more content.