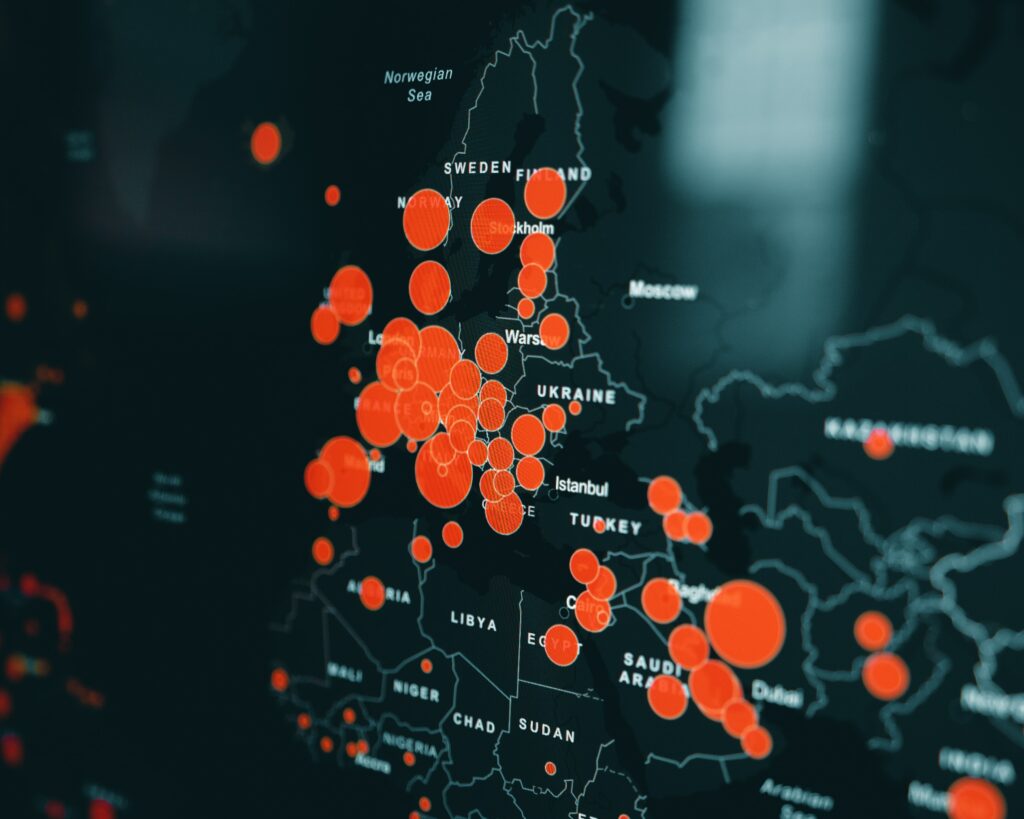
The Reality of Data Breach Take-Down Services in 2024: Do They Work?
The concept of data breach takedown services refers to the efforts made by cybersecurity firms or specialized service providers to mitigate the impact of a data breach by removing unauthorized online content that contains stolen or leaked information. These services often involve the identification, verification, and takedown of sensitive information from websites, forums, chat rooms, and other digital platforms where such data might be shared or sold.
The Reality of Data Breach Take-Down Services in 2024: Do They Work?
Limited Effectiveness of Data Breach Take-Down Services
The feasibility and effectiveness of these services vary significantly based on several factors:
- Access and Influence: Some cybersecurity firms have established relationships with various online platforms, forums, and even dark web sites, which may allow them to request takedowns more effectively. However, this does not guarantee compliance, as the control and willingness of these platforms to cooperate can vary widely.
- Legal and Jurisdictional Challenges: The legal authority and mechanisms to enforce takedown requests can be limited, especially when the platforms hosting the stolen data operate in jurisdictions with lax cybersecurity laws or enforcement practices. In such cases, legal requests might be ignored or refused.
- Nature of Online Content: The internet’s decentralized and borderless nature means that once information is leaked and begins to spread, it can be nearly impossible to remove it entirely. Data can be copied and redistributed across hundreds of channels, forums, and websites, making complete takedown impractical. Efforts to remove data from one site often result in it popping up on another.
- Technical and Operational Capabilities: Some firms specialize in monitoring and tracking the spread of leaked data across the internet, including the dark web and encrypted messaging platforms like Telegram. They use sophisticated tools and techniques to automate the detection of leaked data and initiate takedown processes. However, the effectiveness of these tools can vary, and their operations are often a race against time to mitigate damage.
- Negotiation and Ransom: In certain cases, service providers might negotiate with the threat actors to remove or not publish the stolen data. This approach is fraught with ethical and legal concerns and may not always be successful or advisable.
The notion that breached data, once leaked to the public, is fundamentally impossible to remove entirely from the digital ecosystem is a stark reality in today’s interconnected world. Once sensitive information is exposed and disseminated across various platforms—ranging from public forums and Telegram channels to the more obscure corners of the dark web—it undergoes a process of replication and redistribution that essentially renders it immortal in the digital realm.
Conclusion
This replication process is multifaceted. Breached data is not just shared but also repacked into collections, archived logs, and combo lists, which are then redistributed endlessly. Each cycle of repackaging and redistribution further embeds the data into the fabric of the internet, making it accessible to an ever-widening circle of individuals and entities. The creation of local copies by users who download or otherwise secure this data ensures that even if the original source is somehow taken down, countless other copies remain out of reach, stored in locations that range from the easily accessible to the deeply hidden, including encrypted or anonymized sites behind onion routing (Tor) that obscure their locations and defy precise tracking.
The architecture of the internet itself exacerbates this issue. Its decentralized nature, designed for resilience and redundancy, means that information, once released into this environment, can never be fully retracted. Websites and platforms hosting this data can be located in jurisdictions with little to no legal framework for addressing cybersecurity breaches or enforcing takedown requests, further complicating efforts to mitigate the spread of leaked data.
In this context, data breach takedown services, while offering a valuable service in identifying and attempting to remove leaked data, face insurmountable challenges in achieving complete removal. Their efforts can at best provide a partial remedy, offering insights into the spread and impact of a data breach and, in some cases, managing to remove data from specific sites or forums. However, these successes are often temporary and limited in scope, as the data can quickly reappear elsewhere in the digital ecosystem.
The practical impossibility of completely removing leaked data underscores the critical importance of preventive measures in cybersecurity. Organizations must prioritize safeguarding their digital assets through robust security practices, including regular vulnerability assessments, employee training on phishing and other common attack vectors, and the implementation of strong data encryption and access controls. Additionally, a comprehensive incident response plan that goes beyond attempting data takedown to include steps for mitigating the breach’s impact on affected individuals is essential.
In conclusion, the harsh reality is that once data is breached and leaks into the public domain, it becomes a permanent fixture in the digital landscape, endlessly replicated and redistributed. This underscores the imperative for preventive measures and proactive cybersecurity practices as the most effective strategy for protecting sensitive information. While data breach takedown services can offer some level of mitigation by tracking the spread of leaked information, the ultimate goal should always be to prevent such breaches from occurr