Data Exposure in Code Repositories
As organizations increasingly embrace open source and collaborative approaches to software development, platforms like GitHub, Bitbucket, and SourceForge have become central to their workflows. While these platforms offer considerable benefits, they can also pose significant risks if not used properly. One such risk is the accidental exposure of sensitive data.
Sensitive data exposure happens when confidential information such as configuration files, API keys, database credentials, or other proprietary information is inadvertently made public, often as part of the code committed to public repositories. The exposure of such data poses significant risks, including data breaches, unauthorized access to systems, loss of intellectual property, reputational damage, and regulatory fines.
Understanding the Threat
Public code repositories are ripe targets for cybercriminals. Automated bots scour repositories, hunting for accidentally exposed sensitive information. Once these data are discovered, attackers can use them to gain unauthorized access to systems, steal data, perform actions on behalf of compromised users, or even launch further attacks against an organization’s partners or customers. In some cases, exposed data could also provide attackers with the knowledge required to exploit specific vulnerabilities in an organization’s systems or reveal information about internal architectures, both of which can facilitate more targeted and damaging attacks.
Using a code repository can introduce a number of security risks for an organization, including:
- Data leakage: If an organization uses a code repository to store sensitive data, such as source code, login credentials, or customer data, there is a risk that this data may be accidentally leaked through a misconfigured repository or a compromised account.
- Insider threats: If an organization uses a code repository to collaborate on projects, there is a risk that an employee or contractor may intentionally or accidentally cause a data breach, for example by committing sensitive information to a public repository.
- Third-party risks: If an organization uses a code repository to collaborate with third-party vendors or open-source contributors, there is a risk that a malicious actor may use this access to gain unauthorized access to an organization’s data or systems.
- Malicious code injection: If an organization uses a code repository to manage their software development, there is a risk that a malicious actor may inject malicious code into the repository, which can then be executed on the organizations systems.
- Phishing and Social engineering: a code repository is a platform that is widely used for software development and many developers are active on it. Hackers may use phishing and social engineering tactics to gain access to organization’s sensitive information.
- Compromised dependencies: If an organization uses open-source libraries, they may be unknowingly importing a compromised dependency into their codebase.
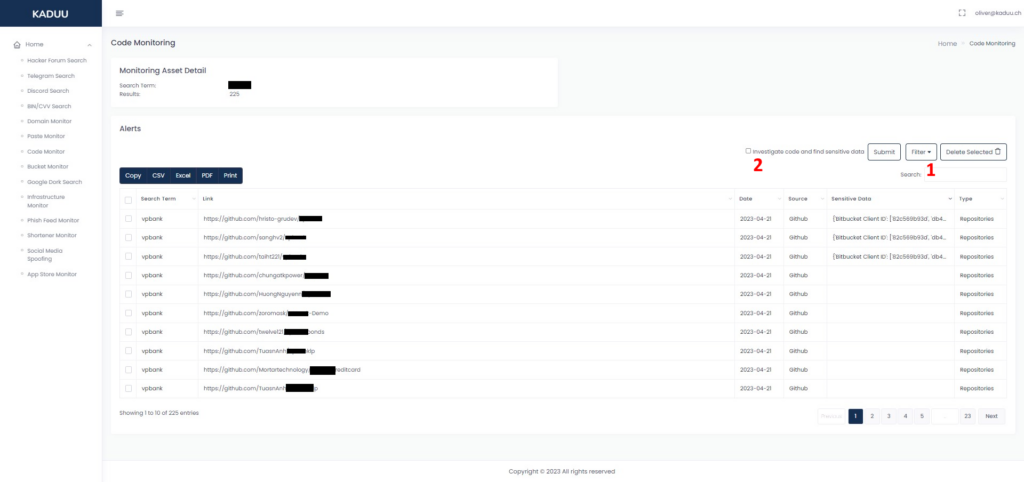
How can you monitor repositories in Kaduu?
Kaduu allows you to capture search terms and check their publication on publicly available repositories. If there is a match, we publish the result with the corresponding link. Kaduu connects to the common repositories once per day for each keyword. After you entered the keyword, the system will find all according repositories containing your keyword. You are then able to either filter for specific file endings (1) or proactively scan the discovered links for sensitive content using a custom regex-list of over 700 possible sensitive findings,